The Situation Report: Your Bank’s Security Probably Stinks

Legacy Threats–They’re Not Just For Government Anymore
My Wall Street outpost reports a new concern among financial institutions–legacy systems. That’s right. Regulations focusing on “too big to fail” have ignited a flurry of mergers and acquisitions in the financial industry, which in turn has created a legacy system vulnerability problem that may be responsible for the majority of data breaches reported to date.
“As banks continue to grow through acquisition, legacy IT systems and their vulnerabilities are also acquired. In many cases, they remain in place for years,” said Sam Kassoumeh, co-founder of SecurityScorecard. The company this week released its 2016 Financial Cybersecurity Report, which studied 7,111 financial institutions including investment banks, asset management firms, and major commercial banks around the world.
The Situation Report received the following FLASH message from SecurityScorecard:
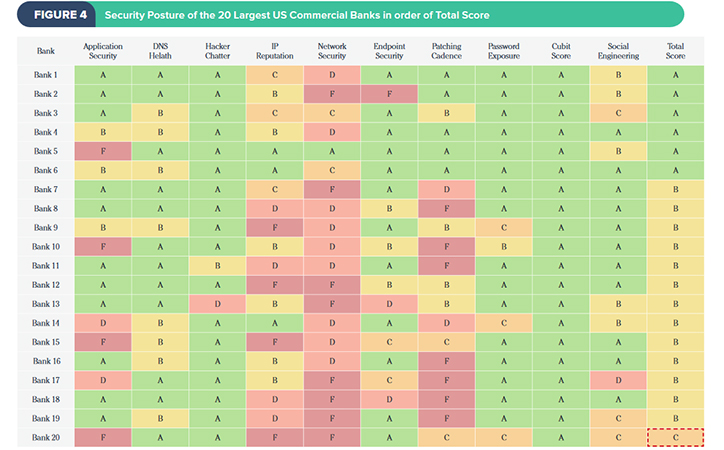
- The U.S. commercial bank with the weakest security posture is one of the top 10 largest financial service organizations in the U.S (by revenue).
- Only one of the top 10 largest banks, Bank of America, received an overall A grade.
- 95 percent of the top 20 U.S. commercial banks (by revenue) have a Network Security grade of C or below.
- 75 percent of the top 20 U.S. commercial banks (by revenue) are infected with malware and a number of malware families were discovered within these banks, including Ponyloader, and Vertexnet.
- Nearly 1 out of 5 financial institutions use an email service provider with severe security vulnerabilities.
-
16 percent use an enterprise cloud storage provider that has received a grade of F in Patching Cadence and a grade of D in Network Security and IP Reputation.
So, you might be wondering what specific vulnerabilities have been discovered at the nation’s biggest banks and financial institutions. Here’s a look.
- 18 out of 20 commercial banks support one or more weak or insecure Transport Layer Security (TLS) cipher suites.
- 15 out of 20 commercial banks have a Secure Sockets Layer (SSL) certificate that is expired.
- 9 out of 20 commercial banks have open File Transport Protocol (FTP) ports found.
-
Generic malware was found in 15 out of 20 commercial banks.
-
Ponyloader (steals credentials and bitcoin wallets) was found in 14 out of 20 commercial banks.
-
Vertexnet (botnet) was found in 9 out of 20 commercial banks.
-
Keybase (keylogger) was found in 8 out of 20 commercial banks.
-
Malware events were detected in all 20 commercial banks over the past 365 days.
-
More than 422 malware events during the past year were detected in just one of the commercial banks.
-
A total of 788 malware events were detected in all 20 commercial banks over the past 365 days.
Defense Acquisition Workers
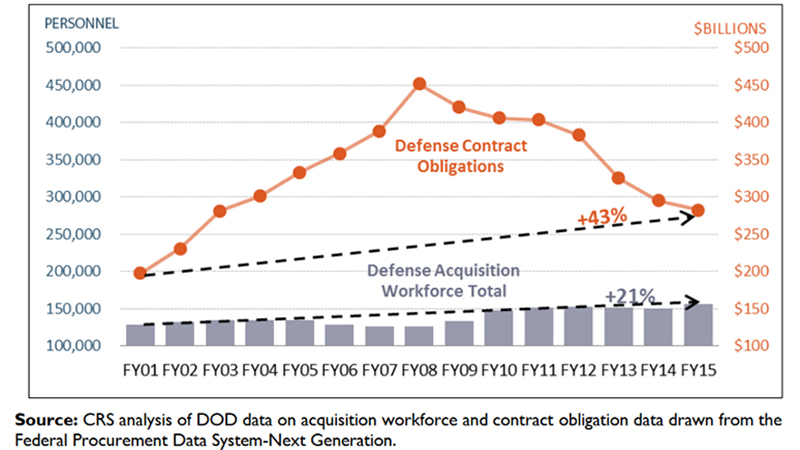
How many Defense Department civilian and military employees does it take to manage the Pentagon’s contract obligations? Well, it appears that nobody inside the five-sided puzzle palace or in Congress really knows the answer to that question.
My E-Ring listening post has intercepted some startling historical data that shows as defense contract obligations reached record highs in 2008, the size of the acquisition workforce in the Defense Department actually shrank to levels not seen since the mid-1990s. And since 2008, as contract obligations have dropped by hundreds of billions of dollars, the Pentagon increased its acquisition workforce by more than 30,000.
While the number of acquisition workers may not be keeping pace with the long-term increase in contract obligations and the massive complexities of the modern acquisition environment, the good news is that the workforce appears better prepared to handle it than ever before.
According to DOD officials, certification and education levels have improved significantly: Currently, more than 96 percent of the workforce meet position certification requirements and 83 percent of the workforce have a bachelor’s degree or higher.