The National Cybersecurity Center of Excellence (NCCoE) and 10 private sector and academia technology partners are collaborating on the Securing Telehealth Remote Patient Monitoring Ecosystem Project. […]
The National Institute of Standards and Technology (NIST) updated Special Publication 800-53, the agency’s main security guidance, for the first time in seven years with new recommendations on supply chain, privacy, and cyber resiliency. […]
The National Institute of Standards and Technology (NIST) is working on a DevOps guidance with an emphasis on the inclusion of security into the process. […]
The National Institute of Standards and Technology (NIST) is seeking comment on its Draft Special Publication 800-133 Revision 2 on Recommendations for Cryptographic Key Generation, which discusses generation of key to be managed and used by approve crypto algorithms. […]
The National Institute of Standards and Technology (NIST) is seeking comments through May 4 on a draft revision of NISTIR 8183, the Cybersecurity Framework Manufacturing Profile, that includes subcategory enhancements established in the agency’s Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1. […]
The Clinical Center at the National Institutes of Health (NIH), which holds tens of thousands of sensitive patient records, needs to develop a secure data backup site, according to a report from the Office of Inspector General (OIG) at the Department of Health and Human Services (HHS). […]
The National Institute for Standards and Technology (NIST) released a report outlining best practices in building the cybersecurity workforce through regional partnerships. […]
The National Institute of Standards and Technology (NIST) Director Walter Copan announced Feb. 19 that just one month after the version 1.0 release of the agency’s privacy framework, NIST is already working on a privacy guide for small- and medium-sized businesses. […]
The National Institute of Standards and Technology (NIST) is seeking public comment on the Feb. 4 draft of its cyber supply chain risk management guidance. […]
A National Institute of Standards and Technology (NIST) draft report on a new program to standardized and centralize cybersecurity regulations is now open for public comment. […]
A new study by the National Institute of Standards and Technology (NIST) revealed that data, algorithms, and application processes are the biggest determinants of facial recognition software’s ability to identify sex, age, and racial background. […]
The National Institute of Standards and Technology (NIST) today released NIST Internal Report 8202, Blockchain Technology Overview. […]
The rising frequency and intensity of cyberattacks on information technology systems that support the government, military, businesses, and critical infrastructure has raised awareness among senior Federal agency managers that security controls cannot be bolted on to systems as an afterthought. Security must be a core part of the design of systems from the beginning, and considered throughout the development lifecycle. […]
Email is a core network application for both the private sector the and government, and has become an essential business communication tool. Since email is nearly ubiquitous and often poorly secured, it also has become a vector for fraud and data theft. Phishing emails can compromise not only Federal networks and databases, but also trust in government communications. […]
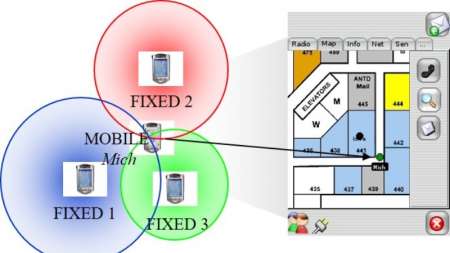
A National Institute of Standards and Technology (NIST) research team collected data from four different smartphone models over an 18-month period to further the development of indoor navigation apps. This type of technology would assist users in finding their way inside unfamiliar buildings, help emergency responders find victims, direct visitors to find specific works of art in large museums, and more. […]
The National Institute of Standards and Technology has released a draft update, Version 1.1, to its Cybersecurity Framework–a guide to help organizations reduce cyber risks. […]
The 18 government agencies with high-impact systems constantly fend off cyberattacks from “nations,” which are groups of hackers sponsored by nation-states. According to a U.S. Government Accountability Office security report, these attacks pose the most serious threat to the security of these systems. […]