The National Security Agency has operated for decades under a well-defined mission: conduct foreign signals intelligence, support military operations, and defend national security systems from attacks. But major changes in the cyber threat landscape during the last few years have forced the agency to embrace a new reorganization strategy that officials argue is urgently needed to defend the nation from an onslaught of state-sponsored hacking attacks.
“We’re increasingly being called to defend the whole of government,” said Curtis W. Dukes, NSA’s information assurance director, during an invitation-only gathering Tuesday of reporters in Washington, D.C. The number of incidents requiring interagency support from NSA’s information assurance directorate—known inside the agency as a Request for Technical  Services—has increased significantly during the last two years, Dukes said.
Services—has increased significantly during the last two years, Dukes said.
“In the last 24 months, there has not been one incident where we did not augment or support” the Department of Homeland Security and Federal contractors doing incident response work, he said. The most notable incidents include the massive data breach at the Office of Personnel Management, the infiltration of the State Department’s email system, an intrusion into unclassified systems used by the Executive Office of the President, a spearphishing attack targeting the Pentagon’s Joint Staff, and the targeting of Sony Pictures Entertainment by North Korean government hackers.
But one of the most damaging attacks involved the likely theft of blueprints to the Pentagon’s newest high-tech jet fighter, the F-35 Joint Strike Fighter. According to Dukes, all indications lead to China, especially since the Chinese military has since fielded a new jet that looks almost identical to the F-35. “We believe [it’s similar] because they actually stole the blueprints,” Dukes said.
NSA21
Long known as the preeminent signals intelligence collection agency in the world, the NSA’s information assurance mission has grown considerably. The foundation of that mission remains blue teaming–defending national security systems; red teaming–hacking systems to find vulnerabilities before adversaries can take advantage of them; and actively hunting for adversaries on national security networks. Put another way, the information assurance mission is to protect, advise, and support.
 That mission is not changing, but the way NSA organizes and operates is. Announced in February by NSA Director Adm. Mike Rogers, NSA in the 21st Century (NSA21) is the agency’s first major reorganization in 15 years. The two-year reorganization will establish six new directorates under a centralized NSA operating framework. Those directorates include: Business Management and Acquisition; Engagement and Policy; Operations; Capabilities; Workforce and Support Activities; and Research.
That mission is not changing, but the way NSA organizes and operates is. Announced in February by NSA Director Adm. Mike Rogers, NSA in the 21st Century (NSA21) is the agency’s first major reorganization in 15 years. The two-year reorganization will establish six new directorates under a centralized NSA operating framework. Those directorates include: Business Management and Acquisition; Engagement and Policy; Operations; Capabilities; Workforce and Support Activities; and Research.
The goal of the reorganization is better integration. The roughly 3,000 people who perform information assurance will be moved into the new Directorate of Operations alongside foreign signals intelligence and cyber defense forces. And Dukes has been given a new role as well: deputy national manager for national security systems.
NSA21 is not the first major reorganization for the once super-secret NSA. In 1999, a group of midlevel managers at NSA produced the New Enterprise Team report, which was highly critical of the agency’s leadership and intelligence failures. Michael Hayden, the NSA director at the time, described the group of 19 managers as “responsible anarchists,” and immediately set out on his “100 Days of Change” initiative. It was the NETeam assessment that led to the creation of the many post-9/11 global surveillance programs, which remain highly controversial.
But it has been the revelations of NSA’s global surveillance activities that has some privacy and civil liberties groups unhappy with the current reorganization plan. They argue that keeping information assurance closely allied with NSA’s foreign intelligence mission leaves open the possibility that the agency can insert vulnerabilities and back doors into systems and commercial products whenever it suits its needs.
Those concerns are not lost on NSA officials, but they insist that the intelligence mission is central to making information assurance more successful in a highly complex, global network environment where attributing attacks is extremely difficult. Dukes and other officials point to NSA’s continuing collaboration with industry giants, like Microsoft and the Linux community, to help improve operating system security, and their routine issuance of unclassified operational risk notifications to private owners of critical infrastructure as areas where the agency’s intelligence insight has been helpful.
This integration will become even more critical as the Internet of Things powers new attacks in an era when, as one official put it, “no network seems to be off limits.”

 The U.S. Department of Health & Human Services Office of the Assistant Secretary for Preparedness and Response created a publicly available interactive map showing the number of Zika virus cases in each state. Zika virus is spread to people primarily through bites from infected Aedes aegypti mosquitoes or through sexual contact. The health impact is greatest on growing fetuses, which can develop a serious birth defect called microcephaly. “Prevention is the first course of action in protecting public health, but people need information to make decisions about what preventive actions to take,” said Este Geraghty,
The U.S. Department of Health & Human Services Office of the Assistant Secretary for Preparedness and Response created a publicly available interactive map showing the number of Zika virus cases in each state. Zika virus is spread to people primarily through bites from infected Aedes aegypti mosquitoes or through sexual contact. The health impact is greatest on growing fetuses, which can develop a serious birth defect called microcephaly. “Prevention is the first course of action in protecting public health, but people need information to make decisions about what preventive actions to take,” said Este Geraghty,  Government employees who attended the hacking conventions of the past had a pretty hard time remaining unnoticed, as many hosted “Spot the Fed” games that rewarded attendees for outing Federal employees. Today’s hacking conventions, like Black Hat and Defcon that took place earlier this month, are creating a much more collaborative environment. “We wanted to do outreach to the hacker community,” Federal Trade Commission chief technologist Lorie Faith Cranor said, adding that her agency wanted to encourage communication and collaboration
Government employees who attended the hacking conventions of the past had a pretty hard time remaining unnoticed, as many hosted “Spot the Fed” games that rewarded attendees for outing Federal employees. Today’s hacking conventions, like Black Hat and Defcon that took place earlier this month, are creating a much more collaborative environment. “We wanted to do outreach to the hacker community,” Federal Trade Commission chief technologist Lorie Faith Cranor said, adding that her agency wanted to encourage communication and collaboration  “We’re trying to make government work better by bringing in top talent and best practices from the technology industry,” said Matt Cutts, USDS software engineer. USDS digitized an external application and internal review process for immigration applications and requests, including the green card renewal application; and launched a digital stamp approval process for agencies processing refugees who have been interviewed and have cleared security and background checks. The digital service team also assists in the day-to-day maintenance of HealthCare.gov, which helps Americans sign up for access to health care provided by
“We’re trying to make government work better by bringing in top talent and best practices from the technology industry,” said Matt Cutts, USDS software engineer. USDS digitized an external application and internal review process for immigration applications and requests, including the green card renewal application; and launched a digital stamp approval process for agencies processing refugees who have been interviewed and have cleared security and background checks. The digital service team also assists in the day-to-day maintenance of HealthCare.gov, which helps Americans sign up for access to health care provided by 
 Eight years ago, Purdue University students could scroll through their BlackBerrys using the institution’s Signals application to learn about their risk of failing a particular class. Now, they can use the school’s new app, Forecast, to learn not only how difficult a class is, but also which courses may be enjoyable for them. Forecast, which was released in March, uses data analysis to help students do well in school and
Eight years ago, Purdue University students could scroll through their BlackBerrys using the institution’s Signals application to learn about their risk of failing a particular class. Now, they can use the school’s new app, Forecast, to learn not only how difficult a class is, but also which courses may be enjoyable for them. Forecast, which was released in March, uses data analysis to help students do well in school and 


 How do you approach managing the cybersecurity of an event as massive and popular as the Olympics? According to Symantec’s vice president for the Americas, Rob Potter, treat the event like a Fortune 100 company. “I think it’s very, very similar, both in dollar amounts and in terms of interaction and people, as a Fortune 100 company for the period of time that the Olympics are,”
How do you approach managing the cybersecurity of an event as massive and popular as the Olympics? According to Symantec’s vice president for the Americas, Rob Potter, treat the event like a Fortune 100 company. “I think it’s very, very similar, both in dollar amounts and in terms of interaction and people, as a Fortune 100 company for the period of time that the Olympics are,”  The Federal government should focus more on defensive cybersecurity measures, work around the regulatory culture of government, and hire more in-house cybersecurity professionals, according to Alex Levinson, information security specialist at Uber. “The government puts a lot of eggs in the offensive basket,” Levinson said. The private sector, which is motivated by profits, differs from the government in that agencies can spend money on developing the latest offensive cyber technologies, because they don’t have to worry as much about money loss,
The Federal government should focus more on defensive cybersecurity measures, work around the regulatory culture of government, and hire more in-house cybersecurity professionals, according to Alex Levinson, information security specialist at Uber. “The government puts a lot of eggs in the offensive basket,” Levinson said. The private sector, which is motivated by profits, differs from the government in that agencies can spend money on developing the latest offensive cyber technologies, because they don’t have to worry as much about money loss,  Agencies must install energy measuring systems to track power usage, complete virtualization and server utilization metrics to ensure that equipment is being used efficiently, and track the use of space in Federal data centers. The new Data Center Optimization Initiative also includes a power usage effectiveness target to increase energy efficiency. Over three years, agencies must close 25 percent of their tiered data centers and 60 percent of their
Agencies must install energy measuring systems to track power usage, complete virtualization and server utilization metrics to ensure that equipment is being used efficiently, and track the use of space in Federal data centers. The new Data Center Optimization Initiative also includes a power usage effectiveness target to increase energy efficiency. Over three years, agencies must close 25 percent of their tiered data centers and 60 percent of their  The company announced Aug. 2 that X-Force Red will consist of hundreds of security experts based in dozens of locations around the world. The team, part of IBM Security Services, will also examine human security vulnerabilities in daily processes and procedures that attackers often use to circumvent security controls. X-Force Red is the latest addition to IBM’s other X-Force divisions and will actively share threat intelligence with IBM X-Force Research, IBM X-Force Exchange threat sharing platform,
The company announced Aug. 2 that X-Force Red will consist of hundreds of security experts based in dozens of locations around the world. The team, part of IBM Security Services, will also examine human security vulnerabilities in daily processes and procedures that attackers often use to circumvent security controls. X-Force Red is the latest addition to IBM’s other X-Force divisions and will actively share threat intelligence with IBM X-Force Research, IBM X-Force Exchange threat sharing platform,  Over U.S. aviation’s 100-year history, 320,000 people have registered to operate manned aircraft. Over the past eight months, 520,000 people have registered to use Unmanned Aerial Vehicles (UAVs). The Unmanned Aircraft Safety Team will include representatives from the drone and aviation industry; this team will analyze safety data from drones and attempt to
Over U.S. aviation’s 100-year history, 320,000 people have registered to operate manned aircraft. Over the past eight months, 520,000 people have registered to use Unmanned Aerial Vehicles (UAVs). The Unmanned Aircraft Safety Team will include representatives from the drone and aviation industry; this team will analyze safety data from drones and attempt to 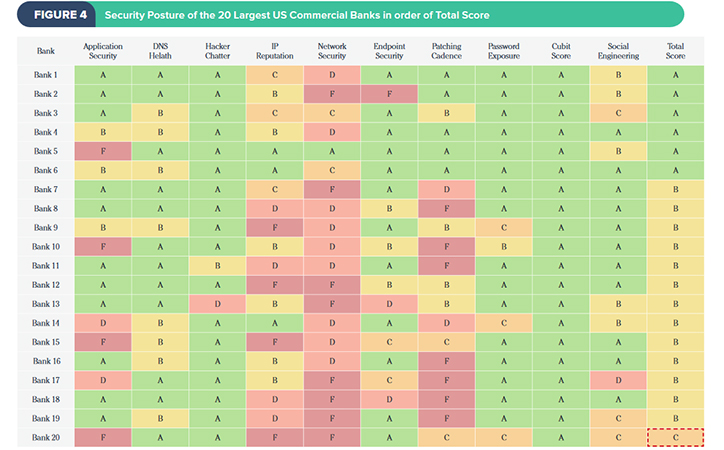
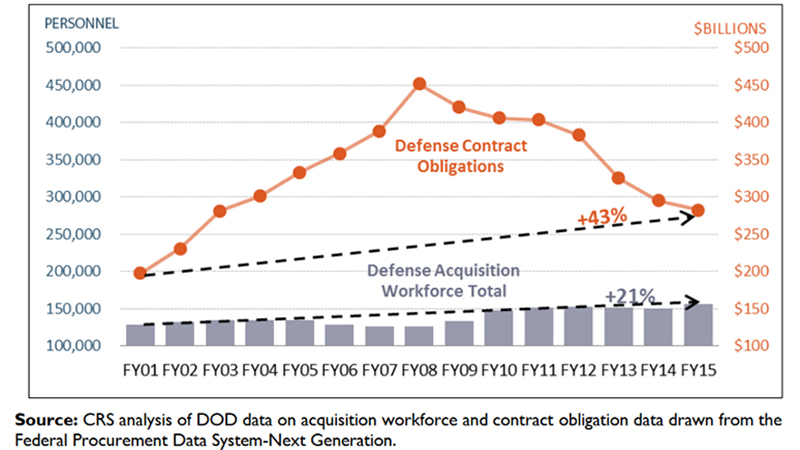
 “[Politicians] are going to have to be developing policies in their local areas to permit a lot of the fruits of new technology,” said Rosabeth Moss Kanter, Ernest L. Many of those policies have to do with preparing for jobs that increasingly require technological experience, such as building infrastructure. “Those jobs don’t necessarily require STEM skills, but they should and they will as technology is increasingly embedded in our infrastructure,”
“[Politicians] are going to have to be developing policies in their local areas to permit a lot of the fruits of new technology,” said Rosabeth Moss Kanter, Ernest L. Many of those policies have to do with preparing for jobs that increasingly require technological experience, such as building infrastructure. “Those jobs don’t necessarily require STEM skills, but they should and they will as technology is increasingly embedded in our infrastructure,”  A sophomore at Watkins Glen High School can use the 45-minute bus ride to her rural home to do her schoolwork with her own personal device. The quarterback of the high school’s football team can complete his assignments on his hour and a half journey to a game at a neighboring school. According to school district Superintendent Tom Phillips, about 20 percent of students in the area come from rural homes that have little or
A sophomore at Watkins Glen High School can use the 45-minute bus ride to her rural home to do her schoolwork with her own personal device. The quarterback of the high school’s football team can complete his assignments on his hour and a half journey to a game at a neighboring school. According to school district Superintendent Tom Phillips, about 20 percent of students in the area come from rural homes that have little or  Telehealth, the delivery of health care services while the patient is at one site, and the licensed health provider is at another site, is here. But what does the future hold in terms of cost, coverage, consumer demands, and legislation? MeriTalk takes an in-depth look at those challenges, and talks with industry leaders about what is not just a novel idea
Telehealth, the delivery of health care services while the patient is at one site, and the licensed health provider is at another site, is here. But what does the future hold in terms of cost, coverage, consumer demands, and legislation? MeriTalk takes an in-depth look at those challenges, and talks with industry leaders about what is not just a novel idea  The Presidential Directive that defined roles and responsibilities of Federal agencies in the event of a cyber incident is being applauded as a step in the right direction by private sector cybersecurity companies. “Clarification on who to contact is important, but the larger challenge is identification and classification of the threat level defined in the schema, and how quickly that determination can be made. It’s a step in the right direction and heightens the need for improved incident preparedness and coordination. We’re getting a step closer to a national cybersecurity weather map.” Much like a weather map, a schema released in conjunction with the directive provides a color-coded graph to measure incident severity and ensure that all parties involved measure their cyber incidents
The Presidential Directive that defined roles and responsibilities of Federal agencies in the event of a cyber incident is being applauded as a step in the right direction by private sector cybersecurity companies. “Clarification on who to contact is important, but the larger challenge is identification and classification of the threat level defined in the schema, and how quickly that determination can be made. It’s a step in the right direction and heightens the need for improved incident preparedness and coordination. We’re getting a step closer to a national cybersecurity weather map.” Much like a weather map, a schema released in conjunction with the directive provides a color-coded graph to measure incident severity and ensure that all parties involved measure their cyber incidents  Chief among these recommendations, which include tips on optimizing IT spending and consolidating data centers, is the need for CIOs to demonstrate transparency. The commission said that improved transparency can also optimize business demand and customer satisfaction. “While not without shortcomings, transparency is a powerful tool for applying the economic forces of supply and demand to IT,”
Chief among these recommendations, which include tips on optimizing IT spending and consolidating data centers, is the need for CIOs to demonstrate transparency. The commission said that improved transparency can also optimize business demand and customer satisfaction. “While not without shortcomings, transparency is a powerful tool for applying the economic forces of supply and demand to IT,”  Many members of Congress can agree that IT modernization is an important problem in need of a solution, but there is less agreement on how exactly to go about it. Two bills focus on the same area of Federal IT needs, but their differences do not necessarily mean that they are contradictory. The symbiotic nature of the bills is evidenced by the fact that some congressmen have cosponsored both bills, such as
Many members of Congress can agree that IT modernization is an important problem in need of a solution, but there is less agreement on how exactly to go about it. Two bills focus on the same area of Federal IT needs, but their differences do not necessarily mean that they are contradictory. The symbiotic nature of the bills is evidenced by the fact that some congressmen have cosponsored both bills, such as  “Postsecondary educational institutions entrusted with student financial aid information are continuing to develop ways to address cybersecurity threats and to strengthen their cybersecurity infrastructure,” wrote Ted Mitchell, the under secretary of the Department of Education. The Gramm-Leach-Bliley Act Safeguards Rule requires universities to: Develop, use, and maintain a written information security program as well as determine employees responsible for coordinating the
“Postsecondary educational institutions entrusted with student financial aid information are continuing to develop ways to address cybersecurity threats and to strengthen their cybersecurity infrastructure,” wrote Ted Mitchell, the under secretary of the Department of Education. The Gramm-Leach-Bliley Act Safeguards Rule requires universities to: Develop, use, and maintain a written information security program as well as determine employees responsible for coordinating the  The Republican Party platform, released during the convention in Cleveland that chose Donald Trump as the nominee, explains the party’s views on technology including broadband expansion, net neutrality, cybersecurity, education, and health care. The platform emphasizes the party’s views that the government should invest in more broadband development. “At the cost of billions, the current administration has done little to advance our goal of universal broadband coverage,”
The Republican Party platform, released during the convention in Cleveland that chose Donald Trump as the nominee, explains the party’s views on technology including broadband expansion, net neutrality, cybersecurity, education, and health care. The platform emphasizes the party’s views that the government should invest in more broadband development. “At the cost of billions, the current administration has done little to advance our goal of universal broadband coverage,”  The House and Senate Intelligence Committees each passed restrictions on the Privacy and Civil Liberties Oversight Board that would restrict its funding, give it jurisdiction only over the privacy of people in the United States, and force it to report to the agencies that it’s overseeing. HR 5077 has passed the House and was referred to the Senate Select Committee on Intelligence. S 3017 was introduced in the Senate last month. “Intelligence authorization bills are neither the appropriate vehicle for authorizing spending for the PCLOB, nor do they pass every year,” Sen. Patrick
The House and Senate Intelligence Committees each passed restrictions on the Privacy and Civil Liberties Oversight Board that would restrict its funding, give it jurisdiction only over the privacy of people in the United States, and force it to report to the agencies that it’s overseeing. HR 5077 has passed the House and was referred to the Senate Select Committee on Intelligence. S 3017 was introduced in the Senate last month. “Intelligence authorization bills are neither the appropriate vehicle for authorizing spending for the PCLOB, nor do they pass every year,” Sen. Patrick  The Situation Report would like to know why the technology revolution has completely bypassed the world of dentistry? Your humble correspondent had a close encounter with a dentist this week and found the entire experience like living through a battle scene in Conan the Barbarian. Now, anybody who sits within 6 feet of me at the MeriTalk office can tell you that this former Marine is one big baby when it comes to
The Situation Report would like to know why the technology revolution has completely bypassed the world of dentistry? Your humble correspondent had a close encounter with a dentist this week and found the entire experience like living through a battle scene in Conan the Barbarian. Now, anybody who sits within 6 feet of me at the MeriTalk office can tell you that this former Marine is one big baby when it comes to 
 The Federal government spends $86 billion a year on outdated Information Technology procurement. Rep. Will Hurd, R-Texas, said the bill would ensure that professionals across Federal agencies have up-to-date technologies. He also said that agencies will now be given an awareness of and access to the savings that modernization
The Federal government spends $86 billion a year on outdated Information Technology procurement. Rep. Will Hurd, R-Texas, said the bill would ensure that professionals across Federal agencies have up-to-date technologies. He also said that agencies will now be given an awareness of and access to the savings that modernization  The Federal government worked to make more incentives for hiring people because it had a shortfall of about 10,000 cybersecurity professionals and the supply was short. Federal CIO Tony Scott told recruits that they didn’t need to devote their whole career to the Federal government. And Scott focused on employee satisfaction by midcareer by making sure they know what their opportunities
The Federal government worked to make more incentives for hiring people because it had a shortfall of about 10,000 cybersecurity professionals and the supply was short. Federal CIO Tony Scott told recruits that they didn’t need to devote their whole career to the Federal government. And Scott focused on employee satisfaction by midcareer by making sure they know what their opportunities  Integrating technology into schools and classrooms certainly has its benefits, from re-engaging disinterested learners to making learning more personalized and improving learning outcomes through analytics. As schools use more and more technology, they also gather more and more personalized data on their students. With this concern in mind, the National Education Association (NEA) released a policy brief earlier this year outlining best practices for
Integrating technology into schools and classrooms certainly has its benefits, from re-engaging disinterested learners to making learning more personalized and improving learning outcomes through analytics. As schools use more and more technology, they also gather more and more personalized data on their students. With this concern in mind, the National Education Association (NEA) released a policy brief earlier this year outlining best practices for  Due to its relatively new and complex nature, there is no straightforward method for categorizing a cyberattack as a digital act of war, according to witnesses at a House Oversight Committee hearing on Wednesday. Witnesses, however, gave no direct definition for what those circumstances would be. “Incidents described as cyberattacks or computer network attacks are not necessarily armed attacks for the purposes of triggering a nation-state’s inherent right of self-defense,” said Aaron Hughes, deputy assistant secretary for cyber policy at the
Due to its relatively new and complex nature, there is no straightforward method for categorizing a cyberattack as a digital act of war, according to witnesses at a House Oversight Committee hearing on Wednesday. Witnesses, however, gave no direct definition for what those circumstances would be. “Incidents described as cyberattacks or computer network attacks are not necessarily armed attacks for the purposes of triggering a nation-state’s inherent right of self-defense,” said Aaron Hughes, deputy assistant secretary for cyber policy at the  Pokémon Go has taken over Washington, D.C., bringing Federal buildings and employees into the gaming sphere. At the Russell Senate Office Building, staffers and senators alike had a chance to catch a Bellsprout if they’re lucky, but contenders must be quick because Pokémon can move around and even run
Pokémon Go has taken over Washington, D.C., bringing Federal buildings and employees into the gaming sphere. At the Russell Senate Office Building, staffers and senators alike had a chance to catch a Bellsprout if they’re lucky, but contenders must be quick because Pokémon can move around and even run  At an information session, NTIS director Avi Bender announced an industry-government venture program, in which private companies can provide data service to Federal agencies. “This is going to give private companies an opportunity to have a conversation with Federal customers,” Bender said. “Many things can happen when you are able to sit in front of someone and interact.” Bender said one goal of the program is to improve the value of big data
At an information session, NTIS director Avi Bender announced an industry-government venture program, in which private companies can provide data service to Federal agencies. “This is going to give private companies an opportunity to have a conversation with Federal customers,” Bender said. “Many things can happen when you are able to sit in front of someone and interact.” Bender said one goal of the program is to improve the value of big data  It’s one of the centerpieces of the Department of Veterans Affairs’ transformation effort. But the so-called strategic sourcing initiative has some front-line IT employees worried that it’s really just a code word for outsourcing their jobs to the private sector. It also refocuses VA on buying best-in-class commercial technologies rather than building custom systems. “This is where the rubber meets the road and it’s the least appreciated and most understaffed area in the VA. It is starting to populate this level with contractors,”
It’s one of the centerpieces of the Department of Veterans Affairs’ transformation effort. But the so-called strategic sourcing initiative has some front-line IT employees worried that it’s really just a code word for outsourcing their jobs to the private sector. It also refocuses VA on buying best-in-class commercial technologies rather than building custom systems. “This is where the rubber meets the road and it’s the least appreciated and most understaffed area in the VA. It is starting to populate this level with contractors,”  The National Oceanic and Atmospheric Administration will launch two satellites to monitor weather and temperature patterns around the globe, but the agency is concerned about potential issues including data gaps following the expiration of previous satellites. In the past, NOAA and the Department of Defense have worked with international organizations to make up for the gaps in weather data. “We have global coordination activities already in place for meteorological activities across all the major [meteorological] organizations in the world,” said Stephen Volz,
The National Oceanic and Atmospheric Administration will launch two satellites to monitor weather and temperature patterns around the globe, but the agency is concerned about potential issues including data gaps following the expiration of previous satellites. In the past, NOAA and the Department of Defense have worked with international organizations to make up for the gaps in weather data. “We have global coordination activities already in place for meteorological activities across all the major [meteorological] organizations in the world,” said Stephen Volz,  Small businesses are prime targets for today’s hackers, according to witnesses testifying at the House Small Business Committee on Wednesday. Because small businesses often don’t have the resources or training to thwart cyberattacks, hackers will choose to go after a large number of them for a small sum, rather than a single, large company that poses a greater challenge. “They often lack the capabilities or the resources to pursue strong, entitywide cyber protections,” agreed Nova Daly, senior public policy
Small businesses are prime targets for today’s hackers, according to witnesses testifying at the House Small Business Committee on Wednesday. Because small businesses often don’t have the resources or training to thwart cyberattacks, hackers will choose to go after a large number of them for a small sum, rather than a single, large company that poses a greater challenge. “They often lack the capabilities or the resources to pursue strong, entitywide cyber protections,” agreed Nova Daly, senior public policy  While some make excuses for Hillary Clinton’s email troubles, it is clear that Americans are not stupid and can see through absurd explanations that attempt to justify the reckless behavior of senior Clinton staff. And the same holds true for every other Cabinet-level official—Democrat or Republican—who put sensitive national security information at risk because of private email use. Your humble correspondent does, in fact, know more than a thing or two about
While some make excuses for Hillary Clinton’s email troubles, it is clear that Americans are not stupid and can see through absurd explanations that attempt to justify the reckless behavior of senior Clinton staff. And the same holds true for every other Cabinet-level official—Democrat or Republican—who put sensitive national security information at risk because of private email use. Your humble correspondent does, in fact, know more than a thing or two about  “IoT approaches will allow people and cargo to be transported more efficiently.” Senators and witnesses alike expressed enthusiasm for IoT’s potential to improve freight, better public transportation, monitor infrastructure, and collect data on transportation operations. “By increasing connectivity and real-time data flows between stakeholders, our transportation network and its users will gain productivity,” said Sen. Deb Fischer, R-Neb. Senators and witnesses also commended the Smart Cities participants, whose projects addressed issues of freight truck shipments, space within the cities, and
“IoT approaches will allow people and cargo to be transported more efficiently.” Senators and witnesses alike expressed enthusiasm for IoT’s potential to improve freight, better public transportation, monitor infrastructure, and collect data on transportation operations. “By increasing connectivity and real-time data flows between stakeholders, our transportation network and its users will gain productivity,” said Sen. Deb Fischer, R-Neb. Senators and witnesses also commended the Smart Cities participants, whose projects addressed issues of freight truck shipments, space within the cities, and  The Defense Health Agency is working on a way for a person injured overseas to have instant access to world-class health care. Electronic health records allow doctors to administer care and patients to access their personal information through their smartphones. David Smith, director of state and local government sales for Citrix, said state governments are improving their operating system landscapes and working to streamline their applications in order to
The Defense Health Agency is working on a way for a person injured overseas to have instant access to world-class health care. Electronic health records allow doctors to administer care and patients to access their personal information through their smartphones. David Smith, director of state and local government sales for Citrix, said state governments are improving their operating system landscapes and working to streamline their applications in order to  College students might be spending their summers slogging away in an unpaid internship, working in retail, or, if they’re lucky, relaxing by the pool. However, even if school isn’t in session, students can still focus on growth and learning. TED Talks are a valuable and free resource
College students might be spending their summers slogging away in an unpaid internship, working in retail, or, if they’re lucky, relaxing by the pool. However, even if school isn’t in session, students can still focus on growth and learning. TED Talks are a valuable and free resource  An update to the Federal Rules of Criminal Procedure, specifically Rule 41, which could automatically take effect in December, is once again bringing up concerns of privacy and security in the digital world. George Washington University Law School research professor Orin Kerr described the lack of avenues for law enforcement when they are seeking to search a computer that is hiding its location, which the changes to Rule 41 seek to fix. The second change to the rule was equally contentious, as opponents claimed that it would allow the government to hack into computers of people that had done
An update to the Federal Rules of Criminal Procedure, specifically Rule 41, which could automatically take effect in December, is once again bringing up concerns of privacy and security in the digital world. George Washington University Law School research professor Orin Kerr described the lack of avenues for law enforcement when they are seeking to search a computer that is hiding its location, which the changes to Rule 41 seek to fix. The second change to the rule was equally contentious, as opponents claimed that it would allow the government to hack into computers of people that had done  Compared to other majors, STEM students are most likely to believe companies will recruit them directly out of college, and 73 percent feel they will receive a good job upon graduation. Using technology in the classroom was reported as improving students’ preparedness for entering the workforce. Eighty-five percent of students surveyed in 2016 felt using technology in classes and as a study tool will make them a stronger job candidate, an increase from 80 percent of
Compared to other majors, STEM students are most likely to believe companies will recruit them directly out of college, and 73 percent feel they will receive a good job upon graduation. Using technology in the classroom was reported as improving students’ preparedness for entering the workforce. Eighty-five percent of students surveyed in 2016 felt using technology in classes and as a study tool will make them a stronger job candidate, an increase from 80 percent of  Rules for drone use took flight this Tuesday after the White House released a set of regulations on the use of these unmanned aerial vehicles. The Federal Aviation Administration’s rules pertain to drones used for hobbies, although the administration also addressed future uses for commercial drones. Drone operators will not be allowed to fly their drones over people and should keep their drone in
Rules for drone use took flight this Tuesday after the White House released a set of regulations on the use of these unmanned aerial vehicles. The Federal Aviation Administration’s rules pertain to drones used for hobbies, although the administration also addressed future uses for commercial drones. Drone operators will not be allowed to fly their drones over people and should keep their drone in  “As Chief of Staff, Kai [Fawn Miller] will work directly with the leadership team to ensure that our daily activities are balanced with our overall mission,” VA CIO LaVerne Council wrote in an email to staff. Council said OI&T is two quarters ahead of its anticipated plan, meeting four of its seven transformation milestones. “Effective immediately, our IT acquisitions team–led by Luwanda Jones–will transition to be the first fully-staffed function in the strategic sourcing organization,”
“As Chief of Staff, Kai [Fawn Miller] will work directly with the leadership team to ensure that our daily activities are balanced with our overall mission,” VA CIO LaVerne Council wrote in an email to staff. Council said OI&T is two quarters ahead of its anticipated plan, meeting four of its seven transformation milestones. “Effective immediately, our IT acquisitions team–led by Luwanda Jones–will transition to be the first fully-staffed function in the strategic sourcing organization,”  “This release allows agencies to use cloud environments for high-impact data, including data that involves the protection of life and financial ruin,” said the FedRAMP announcement, dated June 17. According to the announcement, moderate- and low-impact data account for only about 50 percent of the Federal IT spend, despite consisting of about 80 percent of
“This release allows agencies to use cloud environments for high-impact data, including data that involves the protection of life and financial ruin,” said the FedRAMP announcement, dated June 17. According to the announcement, moderate- and low-impact data account for only about 50 percent of the Federal IT spend, despite consisting of about 80 percent of  New investments in pathogen reduction devices may help reduce the risk of transmitting Zika via blood transfusions. This contract also supports an evaluation of safety for Puerto Rico’s blood system, which is currently supporting Zika virus outbreak response. The system is currently used for platelets and plasma, and the HHS funding will help develop its capabilities
New investments in pathogen reduction devices may help reduce the risk of transmitting Zika via blood transfusions. This contract also supports an evaluation of safety for Puerto Rico’s blood system, which is currently supporting Zika virus outbreak response. The system is currently used for platelets and plasma, and the HHS funding will help develop its capabilities  “[This data] will not necessarily interact with the rest of the cloud platform.” The BDP update will enable operators to manage mission-focused data sets within the existing solution–running custom analytics against the specified data. “The ability for operators to focus the queries against only the data supporting their mission will greatly decrease the time it takes to visualize the results as well as allow further drill down into each result set,” said Bob Landreth, BDP program manager. “We’re about to see quantum leaps in our ability to rapidly develop, deploy, and utilize analytics for CSAAC,”
“[This data] will not necessarily interact with the rest of the cloud platform.” The BDP update will enable operators to manage mission-focused data sets within the existing solution–running custom analytics against the specified data. “The ability for operators to focus the queries against only the data supporting their mission will greatly decrease the time it takes to visualize the results as well as allow further drill down into each result set,” said Bob Landreth, BDP program manager. “We’re about to see quantum leaps in our ability to rapidly develop, deploy, and utilize analytics for CSAAC,”