The Federal government is not traditionally known as being on the bleeding, or even leading, edge of technology. Yet agencies are being challenged every day to innovate, modernize, and “think outside the box”–many times with limited resources. And these challenges are coming from everywhere: from inside the agency, from outside forces such as hackers, and even from constituents who are engaging with agencies in a digitally transformed world. Anyone can tell you it costs a lot of taxpayer money to dream big.
Or does it?
In reality, the big ideas are already tested and validated in the commercial sector. Sometimes, you can match up the big idea with a transformative approach to realize dramatic change…and equally dramatic savings. Most agencies tend to think of IT modernization in strictly hardware and software terms. But modernization is a different strategy…a different way of thinking that includes human beings as well as machines.
All you need to start with is a mission to transform your thinking.
The Mission
To think differently you need to collaborate in entirely new ways. We’ve done this at Dell EMC and we see it all the time within our customer community. The successful groups, the ones that really transform, start by gathering a small but diverse group of people to help. If you’re not the CIO, then invite the CIO. Now add long-tenured IT staff Federal employees, front office administration, a person from finance, one from human resources, a field officer, and then sprinkle in a millennial or two for good measure. You can’t have fresh ideas by using the same thinking and strategies that you use today.
Start with the core mission of your agency, and identify the tech-enabled tools that are helping you accomplish that mission every day. How well are those tools working? How smoothly is the system functioning? Separate them into three lists – good, average, fail – and then triage the “failing” group by assigning priorities based on a function’s criticality to accomplishing the agency’s mission. How much time, money, or resources will it take to correct each problem you’ve identified? Your workgroup will have different ideas about which challenges are merely challenges, and which are outright roadblocks. Allow them to determine your IT priorities.
Traditional, IT-centric projects focused on by managers operating in silos within an agency, simply do not align with an agency’s mission. An antiquated system of servers, storage, and networking cannot deliver information quickly enough or across enough devices. IT priorities have evolved to both create the new information delivery system and make old systems deliver information to that new infrastructure.
We say a future-ready Federal agency is one whose IT infrastructure is the engine of efficiency, not the anchor that prevents it from moving forward. One whose IT infrastructure not only allows change, but is prepared for it. One that enables IT to unlock greater value from its investments, adopt emerging technologies more rapidly, and focus more on new areas of innovation. Digital transformation is an imperative. It is the difference between a successful mission and utter failure.
The transformation has already begun in the workforce and among your constituents. People are witnessing the myriad ways technology is changing the way they conduct daily life, and they expect to have access to those tools when they get to the office. Providing the latest app-enabled tools creates a workforce that grows more connected even as more employees work remotely.
Next Steps
By simplifying and automating an existing IT infrastructure and updating when and where it’s possible, your agency will discover it can actually free up funds for innovation–even with a flat budget. Dell EMC has worked with numerous Federal agencies, here and abroad, to achieve both savings and modernization.
It takes a strong team to break with tradition, think differently, and apply new strategies to doing business. Change doesn’t just happen organically, and it won’t happen if we continue to rely on old modes of thinking. But if there’s a willingness–to spend differently on different priorities driven by a different strategy–then there’s a clear way to IT transformation that aligns with your agency’s mission, not just IT’s mission.


 U.S. thinking about open data is outdated, according to Taavi Kotka, CIO of Estonia, one of the first countries to go fully digital in its government information. “The way we talk about open data, especially here in the U.S., at least how it seems to me, is government takes information form the databases and puts it in some kind of data portals,” he said. “Open data in the meaning that you’re actually going to take data out from the database and put it somewhere in the portal, it’s just so last century.” He explained that digital governments rely on a fully standardized way of storing and using data, as well as a single way of identifying citizens across a variety of fields. “We only use this one unique identifier for the same person,” said Kotka, adding that this ID is used for government, health care, and
U.S. thinking about open data is outdated, according to Taavi Kotka, CIO of Estonia, one of the first countries to go fully digital in its government information. “The way we talk about open data, especially here in the U.S., at least how it seems to me, is government takes information form the databases and puts it in some kind of data portals,” he said. “Open data in the meaning that you’re actually going to take data out from the database and put it somewhere in the portal, it’s just so last century.” He explained that digital governments rely on a fully standardized way of storing and using data, as well as a single way of identifying citizens across a variety of fields. “We only use this one unique identifier for the same person,” said Kotka, adding that this ID is used for government, health care, and  The most important components for smart cities are engaging communities and forging partnerships, according to Federal officials. “That type of goal setting…might give people a concept of what might happen in the future.” One initiative that seeks to bring agencies together to form goals is the Department of Energy’s Better Communities Alliance. “Since 2008, and probably before, we’ve experienced an energy revolution in this country,” said Janine Benner, associate assistant secretary of energy efficiency and renewable
The most important components for smart cities are engaging communities and forging partnerships, according to Federal officials. “That type of goal setting…might give people a concept of what might happen in the future.” One initiative that seeks to bring agencies together to form goals is the Department of Energy’s Better Communities Alliance. “Since 2008, and probably before, we’ve experienced an energy revolution in this country,” said Janine Benner, associate assistant secretary of energy efficiency and renewable  University students have turned to online sources as avenues to avoid purchasing print textbooks, which can cost hundreds of dollars. However, with online access codes, the Student PIRGs report suggests that costs may have caught up with them. Online access codes are serial numbers that students use to unlock learning software, such as digital textbook passages,
University students have turned to online sources as avenues to avoid purchasing print textbooks, which can cost hundreds of dollars. However, with online access codes, the Student PIRGs report suggests that costs may have caught up with them. Online access codes are serial numbers that students use to unlock learning software, such as digital textbook passages,  “Initially they gave us the approval for this and they took it away,” said Matt Jagunic, geographic information systems specialist at NPS. The app highlights activities in the area such as hiking and paddling. However, neither Jagunic nor Mike Land, digital media specialist for the National Park Service Chesapeake Bay, know when the app will return
“Initially they gave us the approval for this and they took it away,” said Matt Jagunic, geographic information systems specialist at NPS. The app highlights activities in the area such as hiking and paddling. However, neither Jagunic nor Mike Land, digital media specialist for the National Park Service Chesapeake Bay, know when the app will return 

 The White House released a progress report on its third Open Government National Action Plan and added new commitments to the plan. “These efforts and more demonstrate the United States commitment to an open government, one that is more transparent, collaborative, and participatory,” Megan Smith and Cori Zarek said. “Over the coming months, the administration will continue to work hard to deliver against all of our open government commitments and to further expand peer exchange opportunities.” The United States is working with other OGP countries to develop technologies that
The White House released a progress report on its third Open Government National Action Plan and added new commitments to the plan. “These efforts and more demonstrate the United States commitment to an open government, one that is more transparent, collaborative, and participatory,” Megan Smith and Cori Zarek said. “Over the coming months, the administration will continue to work hard to deliver against all of our open government commitments and to further expand peer exchange opportunities.” The United States is working with other OGP countries to develop technologies that  Mystery Skype pairs classes from undisclosed locations around the world for video chat sessions. In the span of a class period, students must ask each other “yes” or “no” questions to figure out where their collective Skype dates are from. Toni Olivieri-Barton, Library Technology Educator at Fountain Valley School in Colorado Springs, said many of the partner classes come from within the United States because it is easier to logistically coordinate the time zones; however, sometimes her students will chat with their peers in
Mystery Skype pairs classes from undisclosed locations around the world for video chat sessions. In the span of a class period, students must ask each other “yes” or “no” questions to figure out where their collective Skype dates are from. Toni Olivieri-Barton, Library Technology Educator at Fountain Valley School in Colorado Springs, said many of the partner classes come from within the United States because it is easier to logistically coordinate the time zones; however, sometimes her students will chat with their peers in 


 The Technical Guidelines Development Committee’s cybersecurity working group doesn’t know what to focus on in terms of voting security less than two months from Election Day. “Should we try to continue at this stage or should we simply move on?” Wagner asked the committee. The cybersecurity working group identifies election security principals, looks at election use cases, articulates security best practices, and finds and prioritizes risks. “Most of [the systems] we can handle if you tell us to develop specific requirements.” The committee declined to outline specific requirements in case their best practices
The Technical Guidelines Development Committee’s cybersecurity working group doesn’t know what to focus on in terms of voting security less than two months from Election Day. “Should we try to continue at this stage or should we simply move on?” Wagner asked the committee. The cybersecurity working group identifies election security principals, looks at election use cases, articulates security best practices, and finds and prioritizes risks. “Most of [the systems] we can handle if you tell us to develop specific requirements.” The committee declined to outline specific requirements in case their best practices  The National Telecommunications and Information Administration on Oct. 1 will finish the process of privatizing the Internet’s address book, a task it started in the 1990s. The DNS creates and stores the names of Internet sites. The Federal government has no statutory authority over ICANN. Shifting control to the U.N.–or any intergovernmental body–would leave the Internet vulnerable to geopolitical disputes and
The National Telecommunications and Information Administration on Oct. 1 will finish the process of privatizing the Internet’s address book, a task it started in the 1990s. The DNS creates and stores the names of Internet sites. The Federal government has no statutory authority over ICANN. Shifting control to the U.N.–or any intergovernmental body–would leave the Internet vulnerable to geopolitical disputes and 
 The Senate Committee on Commerce, Science, and Transportation will introduce legislation that aims to fund and expand 911 emergency services at the insistence of the Federal Communications Commission (FCC). 911 emergency networks are dangerously out of date, according to FCC Chairman Tom Wheeler. He said it is time for Congress to transition to the Next Generation 911 (NG911) first envisioned in 1999. Wheeler said the quality of 911 support will deteriorate if Congress does not apply NG911
The Senate Committee on Commerce, Science, and Transportation will introduce legislation that aims to fund and expand 911 emergency services at the insistence of the Federal Communications Commission (FCC). 911 emergency networks are dangerously out of date, according to FCC Chairman Tom Wheeler. He said it is time for Congress to transition to the Next Generation 911 (NG911) first envisioned in 1999. Wheeler said the quality of 911 support will deteriorate if Congress does not apply NG911 
 The White House on Thursday named Brig. Gen. (Ret.) Gregory Touhill as the Federal government’s first chief information security officer, bringing to a close an executive search that has gone on for more than seven months. “In creating the CISO role, and looking at successful organizational models across government, it became apparent that having a career role partnered with a senior official is not only the norm but also provides needed continuity over time,” U.S. CIO Tony Scott said. Touhill enters the job less than four months before the Obama administration leaves office and a new administration is likely to shuffle most of the top national
The White House on Thursday named Brig. Gen. (Ret.) Gregory Touhill as the Federal government’s first chief information security officer, bringing to a close an executive search that has gone on for more than seven months. “In creating the CISO role, and looking at successful organizational models across government, it became apparent that having a career role partnered with a senior official is not only the norm but also provides needed continuity over time,” U.S. CIO Tony Scott said. Touhill enters the job less than four months before the Obama administration leaves office and a new administration is likely to shuffle most of the top national  For the first time in state history, Maryland’s state government website was named the best in the country by the Center for Digital Government’s Best of Web competition. “From day one, our administration has been committed to providing Marylanders with the highest level of customer service across every platform, from in-person to electronic interactions,” said Gov. Larry Hogan. Residents are also able to pay for various government fees online and find information on upcoming events sponsored by
For the first time in state history, Maryland’s state government website was named the best in the country by the Center for Digital Government’s Best of Web competition. “From day one, our administration has been committed to providing Marylanders with the highest level of customer service across every platform, from in-person to electronic interactions,” said Gov. Larry Hogan. Residents are also able to pay for various government fees online and find information on upcoming events sponsored by  Since 2013, more mobile devices have been sold than laptops. Therefore, ransomware is progressing from laptops to mobile devices and IoT devices. Mobile ransomware hackers could use their skills to change the PIN on a user’s phone, overlay an app on an entire phone screen so that the user can’t do anything else on their cellphone, or use the camera app to take pictures or video of the user and threaten to upload the
Since 2013, more mobile devices have been sold than laptops. Therefore, ransomware is progressing from laptops to mobile devices and IoT devices. Mobile ransomware hackers could use their skills to change the PIN on a user’s phone, overlay an app on an entire phone screen so that the user can’t do anything else on their cellphone, or use the camera app to take pictures or video of the user and threaten to upload the  Agencies should be implementing a policy of zero trust when it comes to who is accessing their data, according to Rep. Jason Chaffetz, R-Utah. “Zero trust is one of the things I like to think the private sector figured out a long time ago,” said Chaffetz. Zero trust operates under the principle of “never trust, always verify,” which means that trust is never assumed for any device or user on the system. Chaffetz said the policy is like requiring elementary school students to carry hall passes when they
Agencies should be implementing a policy of zero trust when it comes to who is accessing their data, according to Rep. Jason Chaffetz, R-Utah. “Zero trust is one of the things I like to think the private sector figured out a long time ago,” said Chaffetz. Zero trust operates under the principle of “never trust, always verify,” which means that trust is never assumed for any device or user on the system. Chaffetz said the policy is like requiring elementary school students to carry hall passes when they 

 Since 2012, teachers in grades 3-8 have signed up more than 870,000 students to participate in the national competition. The website has one island per grade level where students play age-appropriate games to learn about Internet safety. After navigating through the islands, students take a quiz based on the
Since 2012, teachers in grades 3-8 have signed up more than 870,000 students to participate in the national competition. The website has one island per grade level where students play age-appropriate games to learn about Internet safety. After navigating through the islands, students take a quiz based on the  The National Institutes of Health announced the winners of the Design by Biomedical Undergraduate Teams Challenge, which included designs for smart pills and disposable sepsis detection chips.Winners excelled across six key categories. The first-place team, from Purdue University, created a “smart pill” to diagnose tuberculosis in children. TB diagnosis is a challenge in low-resources areas because they require trained clinicians and stable electricity–and for children, pediatric diagnostic tests are invasive and painful. The second-place team, from University of Illinois at Urbana-Champaign, developed a disposable
The National Institutes of Health announced the winners of the Design by Biomedical Undergraduate Teams Challenge, which included designs for smart pills and disposable sepsis detection chips.Winners excelled across six key categories. The first-place team, from Purdue University, created a “smart pill” to diagnose tuberculosis in children. TB diagnosis is a challenge in low-resources areas because they require trained clinicians and stable electricity–and for children, pediatric diagnostic tests are invasive and painful. The second-place team, from University of Illinois at Urbana-Champaign, developed a disposable 

 The E-Rate program, which has provided $25 billion in subsidies since 1996 to schools from the Federal government for broadband, internal wiring, and networking equipment, hasn’t correlated with increased test scores among students in North Carolina, a recent study says. The researchers studied how E-rate affected the number of students per Internet-connected computer, SAT scores, and how dollars per student affect test scores from 1999-2013 in public high schools. Under E-rate, schools could apply for grants from the government that would give them a 20 percent to 90 percent discount on telecommunications services and costs associated with Internet wiring, depending on
The E-Rate program, which has provided $25 billion in subsidies since 1996 to schools from the Federal government for broadband, internal wiring, and networking equipment, hasn’t correlated with increased test scores among students in North Carolina, a recent study says. The researchers studied how E-rate affected the number of students per Internet-connected computer, SAT scores, and how dollars per student affect test scores from 1999-2013 in public high schools. Under E-rate, schools could apply for grants from the government that would give them a 20 percent to 90 percent discount on telecommunications services and costs associated with Internet wiring, depending on  In the five years since the government has encouraged agencies to transition to the cloud, spending on cloud-based technologies has increased to about 9 percent, which is a good pace, according to Tom Ruff, vice president of Public Sector America at Akamai. “That was a pretty nice jump given that cloud had some obstacles to begin with,” Ruff said. Agencies struggle with transitioning to the cloud because of security
In the five years since the government has encouraged agencies to transition to the cloud, spending on cloud-based technologies has increased to about 9 percent, which is a good pace, according to Tom Ruff, vice president of Public Sector America at Akamai. “That was a pretty nice jump given that cloud had some obstacles to begin with,” Ruff said. Agencies struggle with transitioning to the cloud because of security  Many of you have heard of “joint operations,” “information operations,” and “intelligence collection activities” when it comes to the world of defense and national security. Well, let me introduce you to the Pentagon’s latest buzz phrase–Identity Activities. “Identity is the summary (or sum total) of multiple aspects of an entity’s characteristics, attributes, activities, reputation, knowledge, and judgments–all of which are constantly evolving,” according
Many of you have heard of “joint operations,” “information operations,” and “intelligence collection activities” when it comes to the world of defense and national security. Well, let me introduce you to the Pentagon’s latest buzz phrase–Identity Activities. “Identity is the summary (or sum total) of multiple aspects of an entity’s characteristics, attributes, activities, reputation, knowledge, and judgments–all of which are constantly evolving,” according 
 What does all of this psychobabble really mean? Well, it means the Pentagon wants to employ data analysis tools that will leverage biographical, biological, behavioral, and reputational data inputs to help the military determine the identity of a person they encounter on the battlefield and whether that person poses any kind of threat.
What does all of this psychobabble really mean? Well, it means the Pentagon wants to employ data analysis tools that will leverage biographical, biological, behavioral, and reputational data inputs to help the military determine the identity of a person they encounter on the battlefield and whether that person poses any kind of threat.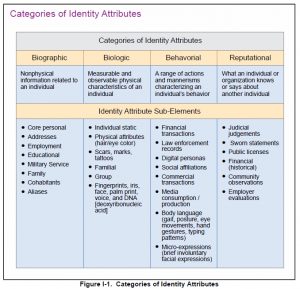
 If the Department of Defense were a private corporation, it would sit at the top of the Fortune 100, a behemoth with more than 2 million employees spread across 5,000 locations and a $36 billion annual IT budget. But it would still be wrestling with what is arguably the most complex enterprise network environment in the world. That is the underlying message in the Defense Department’s new strategy document outlining the department’s vision for its future IT environment. Speaking to reporters, CIO Terry Halvorsen characterized the plan as “a living document” that will change as the department and the
If the Department of Defense were a private corporation, it would sit at the top of the Fortune 100, a behemoth with more than 2 million employees spread across 5,000 locations and a $36 billion annual IT budget. But it would still be wrestling with what is arguably the most complex enterprise network environment in the world. That is the underlying message in the Defense Department’s new strategy document outlining the department’s vision for its future IT environment. Speaking to reporters, CIO Terry Halvorsen characterized the plan as “a living document” that will change as the department and the  Netflix’s new sci-fi series “Stranger Things” has gripped people everywhere, from comic book nerds to those who yearn to go back to the 1980s. As Will’s friends and family members launch a frenzied search for him, their investigation leads them to the nearby Department of Energy facility. Paul Lester, digital content specialist of DOE’s Office of Public Affairs, binge-watched all eight episodes of the first season in a weekend. He wrote a blog post addressing the show’s depiction
Netflix’s new sci-fi series “Stranger Things” has gripped people everywhere, from comic book nerds to those who yearn to go back to the 1980s. As Will’s friends and family members launch a frenzied search for him, their investigation leads them to the nearby Department of Energy facility. Paul Lester, digital content specialist of DOE’s Office of Public Affairs, binge-watched all eight episodes of the first season in a weekend. He wrote a blog post addressing the show’s depiction  The UCaaS provides services such as unified messaging, video calls, call center functionality, and E911 on the cloud, all of which come from Cisco off-the-shelf software. In an interview with MeriTalk, CEO Kevin Schatzle and Mustafa Baig, head of engineering at collab9, described a couple of areas in which collab9’s recently authorized service provides flexibility: bring your own device and contract vehicles. This means that the security for desktops, laptops, smartphones, and other devices already in use in different agencies can be integrated into the
The UCaaS provides services such as unified messaging, video calls, call center functionality, and E911 on the cloud, all of which come from Cisco off-the-shelf software. In an interview with MeriTalk, CEO Kevin Schatzle and Mustafa Baig, head of engineering at collab9, described a couple of areas in which collab9’s recently authorized service provides flexibility: bring your own device and contract vehicles. This means that the security for desktops, laptops, smartphones, and other devices already in use in different agencies can be integrated into the  Active learning includes scientific research or software design to supplement subject matter, computer activities that promote trial-and-error learning, collaboration among students, and writing to produce original ideas and understand concepts. “Throughout the Obama administration the president has recognized that engaging and educating more students in science, technology, engineering, and math subjects will meet a growing need in the nation’s high-tech economy and prepare young people for a range of rewarding careers,” wrote Jo Handelsman, associate director for Science in the OSTP, and Quincy Brown, senior policy adviser for the OSTP, in a blog post. The OSTP wants to hear about incentives given to PK-12 teachers for using active learning methods, investments in professional development opportunities for teachers, and training resources that encourage teachers to use
Active learning includes scientific research or software design to supplement subject matter, computer activities that promote trial-and-error learning, collaboration among students, and writing to produce original ideas and understand concepts. “Throughout the Obama administration the president has recognized that engaging and educating more students in science, technology, engineering, and math subjects will meet a growing need in the nation’s high-tech economy and prepare young people for a range of rewarding careers,” wrote Jo Handelsman, associate director for Science in the OSTP, and Quincy Brown, senior policy adviser for the OSTP, in a blog post. The OSTP wants to hear about incentives given to PK-12 teachers for using active learning methods, investments in professional development opportunities for teachers, and training resources that encourage teachers to use  The Federal Railroad Administration awarded $25 million in grants Tuesday to 11 companies to develop software that will help prevent train collisions. Railroads will use these grants to achieve interoperability through Positive Train Control systems that work to prevent crashes, derailments, intrusions into work zones, and improper switching of lines. “Every dollar we invest in implementing Positive Train Control as quickly as possible is money well spent because ultimately it means fewer accidents and
The Federal Railroad Administration awarded $25 million in grants Tuesday to 11 companies to develop software that will help prevent train collisions. Railroads will use these grants to achieve interoperability through Positive Train Control systems that work to prevent crashes, derailments, intrusions into work zones, and improper switching of lines. “Every dollar we invest in implementing Positive Train Control as quickly as possible is money well spent because ultimately it means fewer accidents and